This summer, hundreds of thousands of people will be preparing to take off while sitting back, relaxing, and using the airplane mode setting on their iPhones. When this setting is activated, the device’s radio frequency (RF) transmission technology is turned off, which severes the user’s connection to their mobile network for the duration of the flight.This function, which was first implemented many years ago as a precautionary safety measure to shield aircraft from what was believed to be tampering with their communications or navigation systems, is also known as flight mode or fly safe mode. In point of fact, many people have exaggerated the severity of this perceived risk to aircraft safety. As a result, the regulations are not as stringent as they once were, and the quality of in-flight Wi-Fi services has increased to the point where they are now usable. Despite this, activating airplane mode continues to be an essential part of the pre-flight procedure.
Nevertheless, researchers at Jamf Threat Labs have recently uncovered and successfully demonstrated an exploit approach that allows an attacker to retain persistence on their victim’s device even when the user thinks they are offline. This technique was developed in response to a vulnerability that was revealed in a previous exploit. The approach, which has not been seen being used in the wild, relies on the successful development of a fake airplane mode “experience” by a hypothetical threat actor. This “experience” causes the device to give the appearance of being offline while in reality it is still functioning normally.
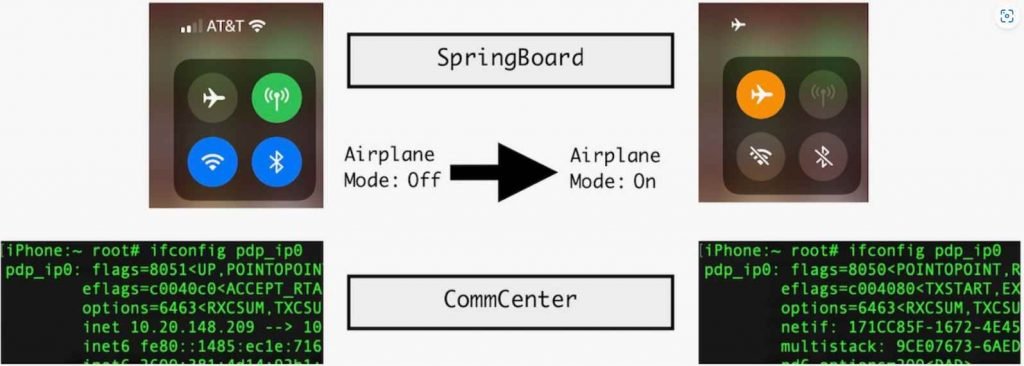
The exploit chain that was put together by Jamf ultimately results in a scenario in which processes that are controlled by an attacker are able to operate in the background undetected and unseen, while the owner of the device is blissfully oblivious that anything is wrong.
SpringBoard, which handles visible changes to the user interface (UI), and CommCentre, which controls the underlying network interface and maintains a feature that enables users to limit mobile data access for certain applications, are the two daemons that are assigned with the process of converting iOS devices to airplane mode. SpringBoard handles visible changes to the UI, while CommCentre manages the functionality. When airplane mode is activated under typical circumstances, the mobile data interface will no longer show IPv4 or 6 IP addresses. Additionally, the mobile network will become disconnected and inaccessible to the user at the level of the user space.
The Jamf team, on the other hand, was able to pinpoint the pertinent area of the target device’s console log and, from that point on, utilize a certain string—”#N User airplane mode preference changing from kFalse to KTrue”—to locate the code that was referencing it. From there, they were able to successfully access the code of the device, at which point they hooked into the function and replaced it with an empty or inactive function. They were able to do this in order to construct a bogus airplane mode, in which the device does not truly get disconnected from the internet and they still have access to it.
After that, they went after the user interface by hooking two unique Objective-C methods to inject a tiny bit of code that changed the mobile connection indicator to make it seem dark, leading the user to believe that it is switched off, and highlighting the airplane mode icon, which is represented by a picture of an airplane.If the hypothetical victim were to open Safari at this point, they would have a good reason to believe that they would be prompted to disable airplane mode or connect to a Wi-Fi network in order to access data. This would be a reasonable assumption given that it seems that aircraft mode is enabled on their device.
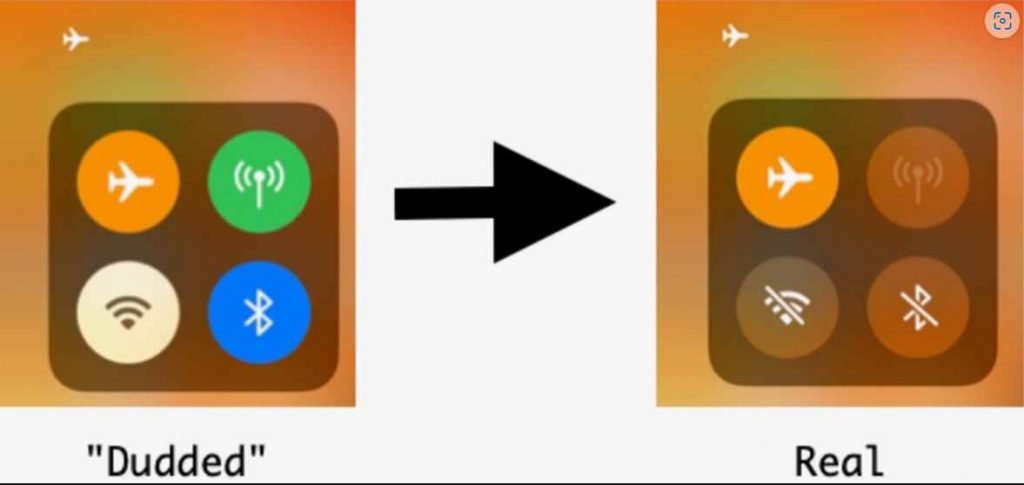
They would receive a separate message asking them to authorize Safari to utilize wireless data through WLAN or mobile, or WLAN alone, which would be a hint that something was wrong. However, since they are really still connected to the internet, they would see this prompt.The Jamf team was aware that this problem needed to be fixed in order for the exploit chain to be successful. As a result, they devised a strategy that enabled them to give the impression to the user that they had been disconnected from mobile data services. This was accomplished by exploiting the CommCenter feature, which blocks mobile data access for specific applications, and then disguising this action as airplane mode by hooking yet another function.
They accomplished this by creating an environment in which the user was presented a prompt to switch off airplane mode, rather than the prompt that they should have seen.The team made use of a feature of SpringBoard that prompts the “turn off airplane mode” notification after being notified to do so by CommCenter. CommCenter, in turn, receives this notification from the device kernel via a registered observer/callback function. This allowed the team to disable Safari’s internet connection without actually turning on airplane mode.
The group then discovered that CommCenter also handles a SQL database file that records the mobile data access status of each program. If an application is prevented from accessing mobile data, that application is marked with a particular flag. They would then be able to selectively prohibit or enable an application’s access to mobile data or Wi-Fi by reading a list of application bundle IDs and obtaining their default settings from this information.
Chain of exploitation
After putting all of this information together, the team had basically developed an attack chain in which their fake airplane mode seems to the victim to be running exactly as the genuine one does, with the exception that non-application programs are allowed to access mobile data.”This hack of the user interface disguises the attacker’s movement by placing the device into a state that is counterintuitive to what the user expects,” he added. “The user expects one thing, but the device behaves in a way that betrays their expectations.” “An adversary could use this to surveil the user and their surroundings at a time when no one would suspect video recording or a live microphone capturing audio,” says one researcher. “This could give an adversary an advantage in a fight.” This is feasible because to the fact that the mobile device in question is still connected to the internet, regardless of what the user interface is trying to convey to them.

According to Covington, the discovery does not fall under the normal responsible disclosure process because the exploit chain does not constitute a vulnerability in the traditional sense. Rather, it is a technique that enables an attacker to maintain connectivity once they have control of the device through another series of exploits. Researchers Did Notify Apple of the Research but no one has responded to request for comment.”
The new attack approach poses a danger, but if it were to be used in anger, it would more likely be used in a targeted attack scenario by a threat actor with very particular aims in mind than in a mass-exploitation event targeting the general public. If it were to be used in anger, however, it would be more likely to be used in anger by a threat actor with very specific goals in mind.As an example, exploitation for the purposes of espionage or surveillance by adversarial actors supported by the government against persons of interest is a scenario that is more likely than exploitation by financially driven cyber thieves.
Despite the fact that the technique is most likely to be used in a targeted attack, it is still important to raise awareness on how device user interfaces, particularly those built by trusted suppliers such as Apple, can be turned against their users. This is because of the inherent trust that people place in their mobile devices.The most crucial thing, according to him, is for consumers and security teams to better understand contemporary attack methods like those shown by the fake airplane mode study. In a sense, this is the next generation of social engineering, and it’s not too unlike to how artificial intelligence is being used to produce bogus testimonials that look to be from well-known celebrities.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.